San Diego CTF 2025 - all pwn challenge
Author: 堇姬 Naup
Preface
This CTF play with Bing Chilling Academies
This CTF’s pwn is so easy, I just spend an hour and a half to solve all pwn challenge. But I still recorded it
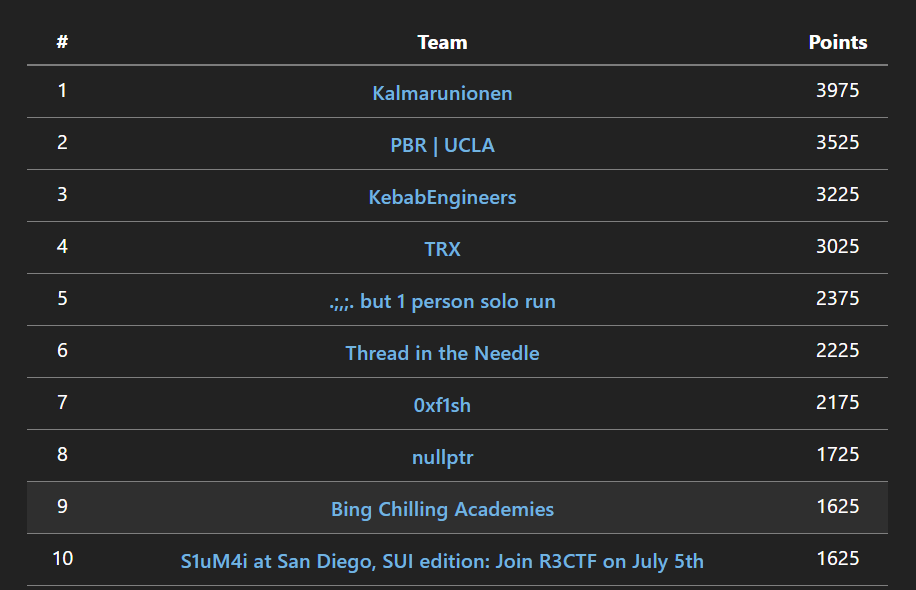
We got rank 9.
Shellphone
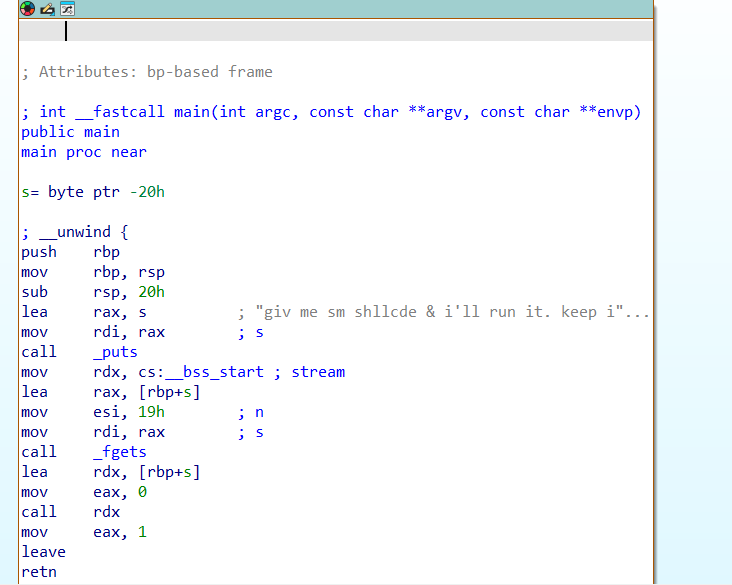
It let you input shellcode (shellcode need to < 0x19 bytes). It will execute your shellcode.
Just use this shellcode can get flag
1 | from pwn import * |
sdctf{omg_i_luv_shlcd}
Gutenberg
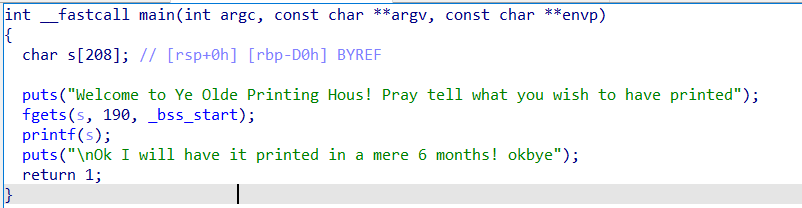
Very simple format string vulnerability.
It give you win function
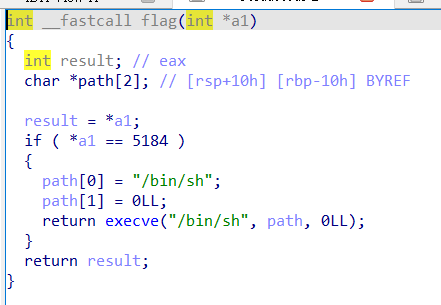
Use fmt overwrite puts@got and you will jump to win function. (You need to jump after *a1 == 5184)
1 | from pwn import * |
sdctf{printing_like_johannes}
ACM Cafe
1 |
|
It give me five times arbitrary write and read.
It is 32bits binary and static linking.
When we look environ, environ have stack address.
So use aaw leak stack address.
We can use stack migration.
I use ROP like this.
It will set :
- eax - 0xb
- ebx - /bin/sh address
- ecx - 0
- edx - 0
1 | pop eax ; ret |
I write it on bss, and use leave; ret gadget mov rsp to my ROP gadget.
We can also overwrite return address to main_loop, getting more chance to write gadget on bss.
More detail go to read my script
1 | from pwn import * |
sdctf{th1s_challenge_f3lt_a_b1t_arbitr4ry}
after all
Need to more difficult pwn challenge…
Thanks all Bing Chilling Academies members.
