pwnable.tw-hacknote
Author: 堇姬Naup
code analyze
main
1 | void __cdecl __noreturn main() |
add_note
可以輸入三項東西
- note_size -> malloc大小note_size
- content -> 內容
1 | unsigned int add_note() |
gdb 進去add note看看,發現了一個chunk有8 byte資料
前四byte -> 0x0804862b -> puts content
後四byte -> 0x0804b1b0(pointer) -> 另一個chunk
接下來malloc一個你自己設定大小的chunk
1 | x/30xw 0x804b198 |
所以要印出的時候,就是去調用puts content,印出後四byte指向的地方
1 | .text:0804862B push ebp |
delete_note
輸入一個index
1 | unsigned int delete_note() |
一次free掉兩塊,並且他沒有清空ptr,所以有double free的問題
print_note
1 | unsigned int print_note() |
印出內容
1 | ---------------------- |
分析
glibc 2.23
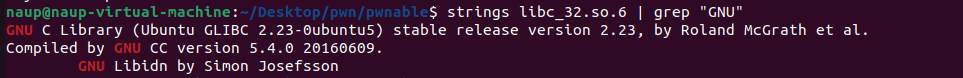
先patchelf把給的libc跟ld patch上去
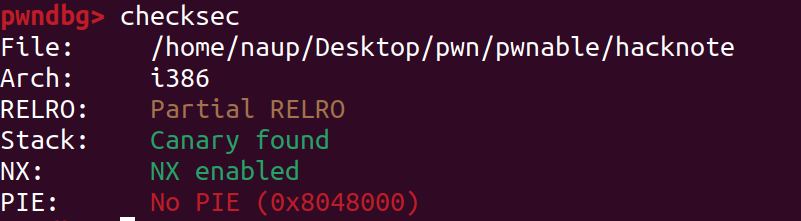
開NX跟
可以用unsorted bin來leak libc,先malloc一塊unsorted bin,free掉後他會指回entry,所以你malloc出來在印出libc就可以了
1 | from pwn import * |
接下來只要能夠嘗試寫掉
前四byte -> 0x0804862b -> puts content
成libc system,那就可以跳到libc上,並且後4byte指向的位置改成sh(由於要4byte,可以用;sh;)
所以這題關鍵就變成了,如何控前面有puts_contenet跟pointer的chunk,他是一個malloc(0x8)大小的chunk,把他free掉後,如果我們add_note(0x8)一個chunk,就可以拿到
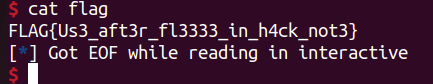
把puts content改寫成system libc,然後把pointer指的位置寫成;sh;,最後print_note,就可以觸發system(‘;sh;’)
script
1 | from pwn import * |